- Politics
- Diversity, equity and inclusion
- Financial Decision Making
- Telehealth
- Patient Experience
- Leadership
- Point of Care Tools
- Product Solutions
- Management
- Technology
- Healthcare Transformation
- Data + Technology
- Safer Hospitals
- Business
- Providers in Practice
- Mergers and Acquisitions
- AI & Data Analytics
- Cybersecurity
- Interoperability & EHRs
- Medical Devices
- Pop Health Tech
- Precision Medicine
- Virtual Care
- Health equity
Locky's (Attempted) Resurgence
The notorious Locky ransomware had been thought dead, until a massive uptick in infections this August.

Born in early 2016, the notorious Locky ransomware had been thought dead or dormant until recently.
In the past month, it has re-emerged with a bang. A group of hackers unleashed over 20 million infected emails in one 24 hours period this week, not long after it was reported that about 60,000 other such emails had appeared in mid-August. Other campaigns trying to push the malware have been bubbling up lately, as well.
The bad actors use various methods: infected Word files that installed it upon closing, fake Dropbox account verification emails, and, as Bleeping Computer refers to them, regular old “boring spam campaigns.”
A Comodo Labs report noted two waves of attacks that present as a file appearing to come as an emailed image from an in-house scanner or printer, as well as a version that appears to come from the French post office. Below is a heat map from the “scanned image” variety of attacks in the Comodo report, demonstrating the locations from which the attacks originated:
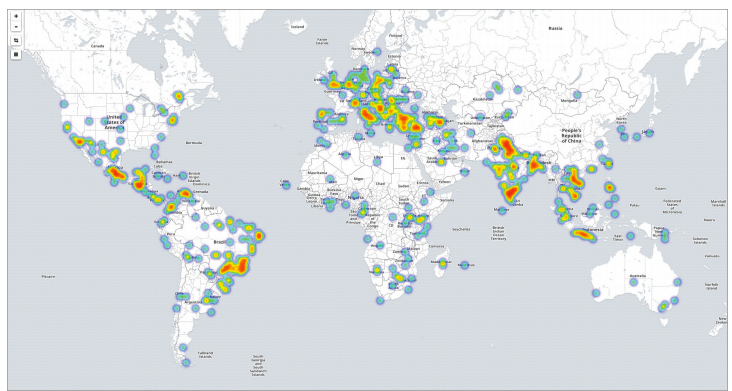
“The simulation of an internal scanner/printer, a second attack just a few days later, and the use of local language elements and a post office domain also continues the trend of increasing sophistication…and adds more credence to the call to act on the recommendation of security experts everywhere,” the report states, recommending a “deny security posture” in which unknown files are prevented from entering your IT infrastructure until verified.
A report from Barracuda on the larger, multi-million-email wave, notes that those attacks come work through impersonation of a trusted user. They present with attachments dubbed “Payment_201708-6165.7z.,” which the security firm identifies to be JavaScript files of the “file encryption/ransomware variety.”
It has been reported by several publications that Locky is the specific ransomware strain that was behind the well-publicized Hollywood Presbyterian Medical Center ransomware attack, as well as another attack on a hospital in Kentucky.
Despite the suddenly-widespread re-emergence of campaigns to compromise systems with Locky, Bleeping Computer claims that statistics the publication obtained “show a minimum spike in new Locky infections compared to the previous week.” Despite this, Locky remains among the trickier, and seemingly resilient, ransomware threats out there.
